

A BlogCast for Victim Advocates
Understanding Digital Abuse:
How Technology is Used to Control and Harm Victims
Episode/Blog Transcript
Understanding Digital Abuse:
How Technology is Used to Control and Harm Victims
Note: We recognize the depth of your experience, but even the most seasoned professionals occasionally need a reminder or a quick refresher.
In today's hyper-connected world, technology can be a powerful tool for safety, communication, and connection. Unfortunately, it can also be weaponized by abusers to control, harass, and monitor their victims. For victim advocates working alongside law enforcement, understanding digital abuse is crucial to helping survivors stay safe — both online and offline.What is Digital Abuse?
Digital abuse is a form of emotional and psychological abuse where technology is used to intimidate, threaten, stalk, or control another person. While it can happen in any abusive relationship, it’s especially common in intimate partner violence (IPV) situations.
Unlike traditional abuse, which often requires physical proximity, digital abuse can happen anywhere, at any time, extending the reach of the abuser and making victims feel like they can never truly escape.
Common Tools and Tactics Used in Digital Abuse
1. GPS Tracking and Location Monitoring
- Abusers may use tracking devices hidden in vehicles, phones, or personal items to monitor a survivor’s location.
- Some apps designed for "family safety" or "phone finding" are misused to stalk victims without their knowledge.
2. Spyware and Stalkerware
- Software secretly installed on devices can allow abusers to read texts, monitor calls, track internet use, and even access cameras and microphones.
- Victims often don't realize their privacy has been breached because these apps run silently in the background.
3. Social Media Harassment
- Abusers may use fake accounts to monitor or harass victims.
- They may also impersonate the victim online, post private photos or information, or spread rumors to isolate the survivor socially and professionally.
4. Texting, Calling, and Messaging Abuse
- Constant, threatening, or manipulative messages keep victims under psychological pressure.
- Some abusers use multiple phone numbers or messaging apps to bypass blocks.
5. Financial Digital Control
- Abusers may control online banking access, steal digital identities, or track spending to maintain financial dominance over a victim.How Advocates Can Help Survivors Stay Safe in the Digital Age
🌟 Start with Awareness and Validation
- Validate the survivor's fears — technology-facilitated abuse is very real.
- Let them know it's not "paranoia" to be concerned about online monitoring.
🔍 Conduct a Tech Safety Assessment
- Ask if the survivor feels their phone, email, social media, or devices are being monitored.
- Encourage them not to immediately abandon their current device if they suspect it's compromised — it could alert the abuser. Develop a safer tech plan carefully.
🔒 Recommend Safe Tech Practices
- Suggest using secure passwords and two-factor authentication.
- Encourage checking app permissions and settings on devices.
- Recommend creating new email and social media accounts from safe, unknown devices if needed.
📱 Provide Resources for Digital Safety
- Connect survivors with resources like the National Network to End Domestic Violence’s (NNEDV) Safety Net Project, which offers detailed guidance on tech safety.
- Recommend safe browsing apps and tools designed for survivors.
🤝 Collaborate with Law Enforcement and IT Experts
- Work with cybercrime units or digital forensics experts if available.
- Help victims document digital harassment — screenshots, call logs, and messages can be critical evidence.
Final Thoughts: Empowerment Through Knowledge
Technology-facilitated abuse can feel invisible and overwhelming, but with the right information, survivors can reclaim their digital safety and autonomy. As victim advocates, our role is to equip them with knowledge, options, and unwavering support every step of the way.
By staying informed about the evolving tactics of digital abuse, we can help break the cycle of control and empower survivors to step into a safer future.
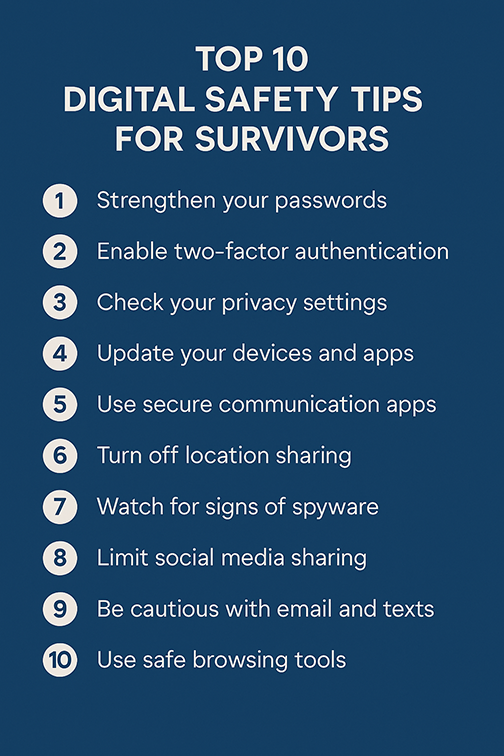
Download "Top 10 Digital Safety Tips for Survivors" here. Edit it for your agency and share with those you serve.
On behalf of the team at Visible Digital Solutions, thank you for your service!
_____________________
Learn how our eVAC program can assist you with your victims of crime. Click here for more information.
RECENT POSTS
Tap the three lines to see Post list.
Copyright - Visible Digital Solutions LLC | Privacy Policy